Enabling Versioning, MFA Requirement and Permissions for S3 Bucket
Versioning gives you the ability to maintain various versions of one object in the same chosen bucket. Here we are going to learn the way for enabling object versioning on a specific bucket of your choice.
How can we enable or disable versioning on a bucket?
-
- Log into the Management Console and go to the S3 console by following this link https://console.aws.amazon.com/s3/.
- From the Bucket namelist, select the bucket which you would like to have versioning enabled for.
aws s3 bucket name list
-
- Select Properties.
-
- Select Versioning.
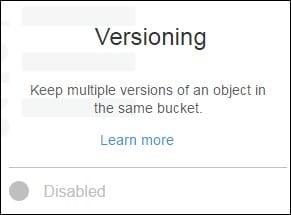
s3 bucket versioning – disabled
- Select the Enable versioningchoice or the Suspend versioning choice, and click on the save button.
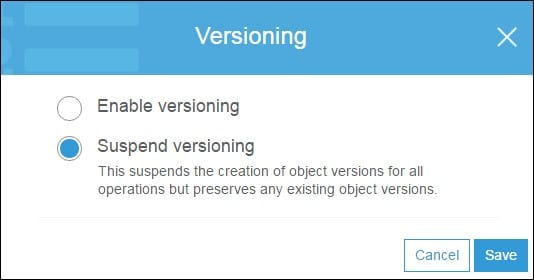
s3 bucket – suspend versioning
Important
Multi-Factor Authentication can be utilized with the enablement of versioning. For using Multi-Factor Authentication while versioning is enabled, an AWS account’s access keys must be given as well as a valid code coming from the same MFA device used for the account, so that an object could be deleted completely or so that you choose either suspension or reactivation of versioning. MFA Delete needs to be enabled for the usage of MFA while versioning is enabled, but it’s not possible to go ahead and enable MFA Delete through AWS Management Console. The CLI or API should be used for enabling the MFA Delete.
How to get the MFA Requirement:
– MFA-protected API access is supported by S3
-Having this feature gives us the ability to enable MFA for the access allowed to S3 resources
– MFA allows for an additional security level to be applied to the AWS environment that you’re working with.
MFA is a:
-Security feature
-It asks of the users to admit their physical possession for a given MFA device
-It asks users to provide it with a valid MFA code
-MFA can be required by the users in case of the need for setting requests to access their S3 resources.
-MFA requirement may be enforced through the aws:MultiFactorAuthAge key in a specific bucket policy
-IAM users may now get the ability to access and go to their S3 resources through their temporary credentials which were given by the STS
-MFA code is asked to be provided when the STS request is being made by the user
As soon as S3 gets a request with a specific multi-factor authentication, the aws:MultiFactorAuthAge key will give a number which shows how many seconds ago did the credential get created.
In case this credential had not been created by an MFA device, it will be absent which means its = null.
-If you wish, you can get the chance to add a condition for checking this number in your bucket policy, just like the example below shows. By doing so, your bucket policy will start denying all S3 operations made on the /FirstFile folder which is found in the creater-admin bucket in the case that this request was not authorized through MFA.
{
"Sid": "",
"Effect": "Deny",
"Principal": "*",
"Action": "s3:*",
"Resource": "arn:aws:s3:::creater-admin/FirstFile/*",
"Condition": { "Null": { "aws:MultiFactorAuthAge": true }}
}
The Null condition in the Condition block evaluates to true if the aws:MultiFactorAuthAge key value is null, indicating that the temporary security credentials in the request were created without the MFA key.
-The following bucket policy is an extension of the preceding bucket policy. It includes two policy statements. One statement allows the s3:GetObject permission on a bucket (creater-admin) to everyone. Another statement further restricts access to the creater-admin/FirstFile folder in the bucket by requiring MFA.
{
"Sid": "",
"Effect": "Allow",
"Principal": "*",
"Action": ["s3:GetObject"],
"Resource": "arn:aws:s3:::creater-admin/*"
}
-Also, a numeric condition could be relied on for limiting duration of validity for the aws:MultiFactorAuthAge key, without taking into consideration how long the security credential’s lifetime was upon the authentication of this request. In the following example code line we can see how this bucket policy checks when the temporary session had been created. The policy will further deny all possible operations in case the aws:MultiFactorAuthAge key value shows that this temporary session had been for longer than 3600 seconds.
{ {
"Sid": "",
"Effect": "Deny",
"Principal": "*",
"Action": "s3:*",
"Resource": "arn:aws:s3:::creater-admin/FirstFile/*",
"Condition": {"NumericGreaterThan": {"aws:MultiFactorAuthAge": 3600 }}
}}
{ {
Cross-Account Upload Permissions While Owner Has Full Control
-Owners have the ability to grant permission to other accounts for uploading objects to their bucket
-But as bucket owners they should have total control of the objects being uploaded to their chosen bucket
The policy below states that a chosen account (888888888888) will be denied when uploading objects if he does not grant the bucket owner total control access. The “creater-admin” bucket owner is identified by his chosen email: owner@amazon.com.
StringNotEquals condition shows that the s3:x-amz-grant-full-control condition key for the sake of expressing the requirements.
{
"Sid":"111",
"Effect":"Allow",
"Principal":{"AWS":"888888888888"},
"Action":"s3:PutObject",
"Resource":"arn:aws:s3:::creater-admin/*"
},
{
"Sid":"112",
"Effect":"Deny",
"Principal":{"AWS":"888888888888" },
"Action":"s3:PutObject",
"Resource":"arn:aws:s3:::creater-admin/*",
"Condition": {
"StringNotEquals": {"s3:x-amz-grant-full-control":["emailAddress=owner@amazon.com"]}
}}
{
"Sid":"111",
"Effect":"Allow",
Permissions for S3 Inventory and S3 Analytics
-S3 inventory: for lists of objects in a bucket
-S3 analytics export: for output files of the data being utilized in analysis
-Name of the bucket which the inventory lists objects for: source bucket
-Name of the bucket where both the inventory file and the analytics export file get written: destination bucket
A bucket policy needs to be created and set for destination bucket during the stages of:
-Setting up inventory for a bucket
-Setting up its analytics export
In the below example, S3 permission is given for writing objects which are referred to as: PUTs from source bucket of account “8888888888” to the destination bucket.
Such a bucket policy is used on destination bucket at the stage of setting up both the S3 inventory and S3 analytics export.
{
"Sid":"InventoryAndAnalyticsExamplePolicy",
"Effect":"Allow",
"Principal": {"Service": "s3.amazonaws.com"},
"Action":["s3:PutObject"],
"Resource":["arn:aws:s3:::destination-bucket/*"],
"Condition": {
"ArnLike": {
"aws:SourceArn": "arn:aws:s3:::source-bucket"
},
"StringEquals": {
"aws:SourceAccount": "8888888888",
"s3:x-amz-acl": "bucket-owner-full-control"
} }}