Locking an S3 Object
For locking an S3 Object go over the steps listed in the following tutorial.
With Amazon S3 object lock, you can store objects in Amazon S3 using a write-once-read-many (WORM) model. You can use Amazon S3 object lock to prevent an object from being deleted or overwritten for a fixed amount of time or indefinitely.
Before you lock any objects, you have to enable a bucket to use Amazon S3 object lock. You enable object lock when you create a bucket. After you enable Amazon S3 object lock on a bucket, you can lock objects in that bucket. When you create a bucket with object lock enabled, you can’t disable object lock or suspend versioning for that bucket.
To lock an Amazon S3 object:
- Login to the Management Console and head to the S3 console at https://console.aws.amazon.com/s3/.
- From the Bucket name list, start by choosing the name of the bucket you want to work with.
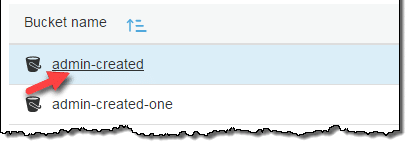
Locking an S3 Object – Select a Bucket
- From the Name list, select the name of the object for placing a lock on.
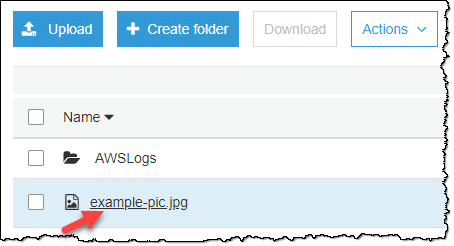
Locking an S3 Object – Select an Object
- Click on Properties.

Locking an S3 Object – Select on Bucket Properties Tab
- Select Object lock.
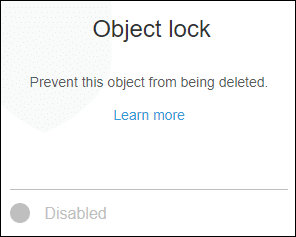
Locking an S3 Object – Go to Object Lock Section
- Select retention mode. The Retain until date may be changed. A legal hold may also be enabled.
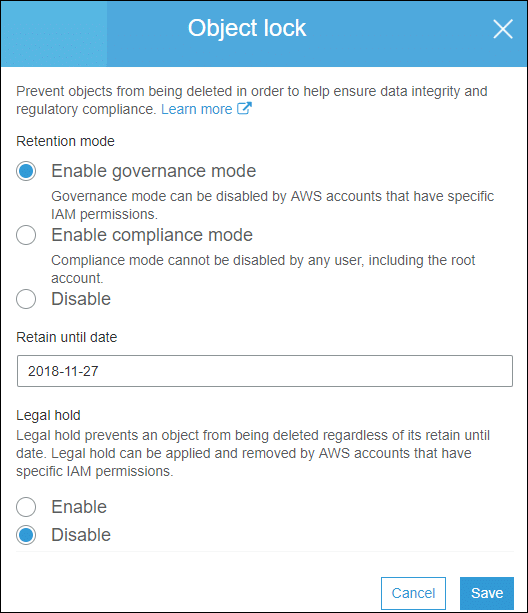
Locking an S3 Object – Change Object Lock Properties
- Click the Save
S3 Object Locks Management:
It allows you to store objects in Amazon S3 by the following model: write once, read many (WORM).
It can be used for performing the following options on the object lock status of objects:
– View
– Configure
– Manage
Viewing Lock Information:
Object lock status can be viewed through GET Object or HEAD Object commands, that give back object version’s retention mode (Retain Until Date) and legal-hold status.
s3:GetObjectRetention permission is required for viewing object version’s retention period and mode.
s3:GetObjectLegalHold permission is required for viewing object version’s legal hold status.
When we GET or HEAD an object version without the required permissions for viewing lock status, this request will still succeed. (information that you don’t have permission to view isn’t returned)
If a bucket has a default retention configuration and you would like to view it, you will need to request its object lock configuration. In order to do so, you will need to have the s3:GetBucketObjectLockConfiguration permission. (In case of requesting for object lock configuration for a bucket with no object lock, an error shall be returned)
S3 inventory reports can be configured for all the bucket’s objects to have the below:
– Retain Until Date
– Object lock Mode
– Legal Hold Status
Bypassing the Governance Mode:
You can perform operations on object versions that are locked in governance mode as if they were unprotected if you have the s3:BypassGovernanceRetention permission.
Some of those operations are:
– Deletion of an object version
– The shortening of retention period
– The removal of object lock through adding a new lock of empty parameters
By clearly stating in the request that you wish to bypass a governance mode, you will be able to bypass it. To do so, you will need to include x-amz-bypass-governance-retention:true header along with the request. Management Console will directly apply this header for all requests that are placed through the console with permission to bypass governance mode.
By bypassing governance mode, the object version’s legal hold status will not be affected whatsoever. When a legal hold is enabled on an object version, it will remain in force and not allow any requests to overwriting and deleting object version.
Configuring Events and Notifications:
S3 events may be configured for object-level operations through the utilization of an object lock bucket. In the case the following calls have object lock metadata: PUT Object, HEAD Object, and GET Object, their events will contain the values of those metadata. In case the object lock metadata gets’ either added or updated for a specific object, events will also be triggered due to those actions. Such events will take place when you choose:
– PUT or GET object retention
– The legal-hold information
AWS CloudTrail will help you utilize the event notifications in order to start:
– Tracking access to object lock configurations and data
– Tracking changes to object lock configurations and data
– Generating alerts based on this data
How to Set Retention Limits:
Through a bucket policy, maximum and minimum allowable retention periods can be set for your bucket. This is done with the help of the condition key of: s3:object-lock-remaining-retention-days. In the bellow bucket policy, we have a minimum retention period of ten days being set.
{
“Version”: “2012-10-17”,
“Id”: “<Policy1436912751980>“,
“Statement”: [
{
“Sid”: “<Stmt1436912698057>“,
“Effect”: “Deny”,
“Principal”: “*”,
“Action”: [
“s3:PutObjectRetention”
],
“Resource”: “arn:aws:s3:::<example-bucket>/*”,
“Condition”: {
“NumericGreaterThan”: {
“s3:object-lock-remaining-retention-days”: “10”
}
}
}
]
}
When a bucket is the destination bucket for a replication policy, in order to set up retention periods for object replicas, the following action must be included in the bucket policy: s3:ReplicateObject.
Delete Markers + Object Lifecycles:
It’s not possible to delete a protected object version, but there’s the choice to create a delete marker for it.
By putting a delete marker on an object, you will still not be able to delete any of its versions, yet it causes Amazon S3 to work so as if the object was actually deleted.
It’s important to know the following:
– WORM-Protection does not accompany delete markers no matter what the retention period or the legal hold that are on this object.
– On protected objects and placing delete markers, configurations for lifecycle management configurations remain normally functional.
– Lifecycle configuration does not cause deletion or overwriting of Protected object versions.
Obtaining an S3 Object Lock with Replication:
Follow the below steps to achieve the following options across buckets that are found in different or similar Regions:
– Automatically enabling object lock + replication
– Asynchronously copying locked objects + retention metadata
With replication, source bucket objects get replicated to another destination bucket.
For setting up the object lock + replication, select one of the below ways:
First Option: Enabling the object lock firstly.
- Go first and enable object lock either for: destination bucket only, or source and destination bucket both together.
- Start setting up replication between: source bucket and destination bucket.
Second Option: Setting up replication firstly.
- Start by setting up replication between: source bucket and destination bucket.
- Then, get the object lock enabled for: destination bucket only, or both source bucket and destination bucket.
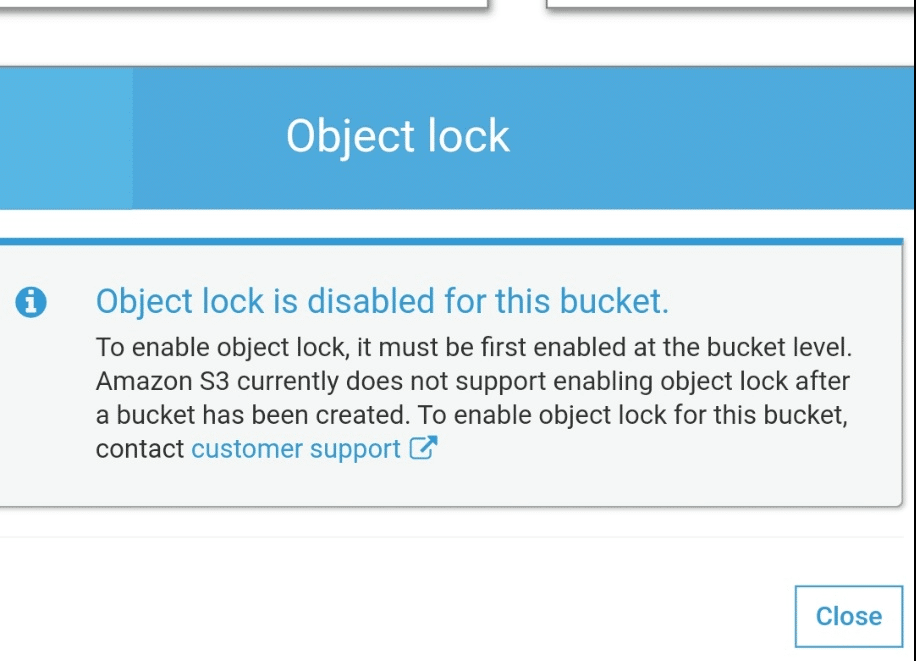
Locking an S3 Object – Object Lock Disabled
For finishing step 2, you are going to have to contact AWS Support, to check that replication has a perfect configuration.
Prior to contacting AWS Support, the below requirements must be reviewed for the set-up of object lock with replication:
- Object lock should be enabled on the destination bucket.
- You must grant two new permissions on the source S3 bucket in the AWS Identity and Access Management (IAM) role that you use to set up replication.
Two new permissions:
– s3:GetObjectRetention
– s3:GetObjectLegalHold.
A role would satisfy the requirement when there’s s3:Get* permission on it.