How to create CMKs in Custom Key Store?
Upon the creation of a custom key store, it is possible to now create customer master keys in that key store. Those customer master keys need to be symmetric with key material that the KMS generates. It’s not possible to actually create asymmetric customer master keys or CMKs with any of the imported key material.
You can utilize and manage the customer master keys in the custom key store just exactly as how you would utilize and manage any customer master key in the KMS. As an example, the below options can be made:
- Utilizing customer master keys for cryptographic operations
- The setting up of IAM and key policies on customer master keys
- The creation of aliases which get associated with customer master keys
- The attachment of tags to customer master keys
- The enabling and disabling of customer master keys
- The scheduling of deletions for customer master keys
The creation of a customer master keys in a custom key store, you must first connect the custom key store to its CloudHSM cluster which contains a minimum of two active HSMs in multiple differing Availability Zones. You will need to go to the custom key stores page in Management console in order to discover connection status and HSMs’ number. Along with the API operations, rely on DescribeCustomKeyStores operation for the verification of the connection of custom key store. In order to know the value of active HSMs in cluster, you will need to utilize CloudHSM DescribeClusters operation.
With the creation of a customer master key in the custom key store, KMS is going to create this customer master key in the KMS. However, key material for this customer master key is created in the associated CloudHSM cluster. KMS logs into the cluster with the kmsuser CU you made, and later creates a 25-bit continuous, non-extractable AES symmetric key in this cluster. KMS will choose the value of key label attribute (only visible in the cluster) to ARN of the CMK.
Upon the success of the command, key state of the new customer master key gets Enabled and its takes the origin of AWS_CLOUDHSM (cannot be changed after being created). Once viewing a customer master key in a custom key stor or through the DescribeKey operation, the following can be seen:
- Typical properties
- Key ID
- Key state
- Creation date
- Custom key store ID
- AWS CloudHSM cluster ID
In the attempt of creating a customer master key in the custom key store and it fails, try to head to the error message for getting help in determining what the main cause was.
The following problems may be indicated:
- The custom key store may not be connected, showing the “CustomKeyStoreInvalidStateException” error message.
- The associated CloudHSM cluster may not possess the two active HSMs which are needed for your operation, showing the “CloudHsmClusterInvalidConfigurationException” error message.
Creating a Customer Master Key in a Custom Key Store Using the Console:
The below procedure shows the way to creating a CMK in a custom key store.
Step 1.
Login to the Management Console and go to the Key Management Service console through the following link https://console.aws.amazon.com/kms.
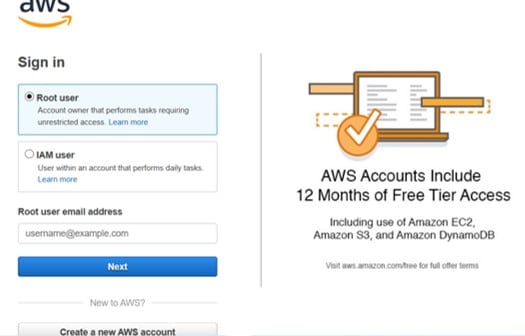
Create CMKs in Custom Key Store – Management Console
Step 2.
For changing your Region, head to the Region selector from the top-right corner.
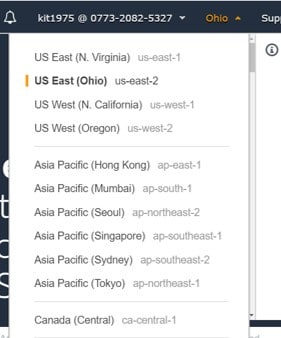
Create CMKs in Custom Key Store – Change your region
Step 3.
From the navigation pane, select Customer managed keys.
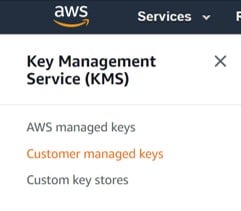
CMK – customer managed keys
Step 4.
Click on Create key.
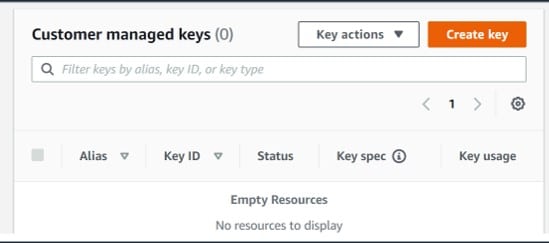
Create CMKs in Custom Key Store – create key
Step 5.
Select the Symmetric
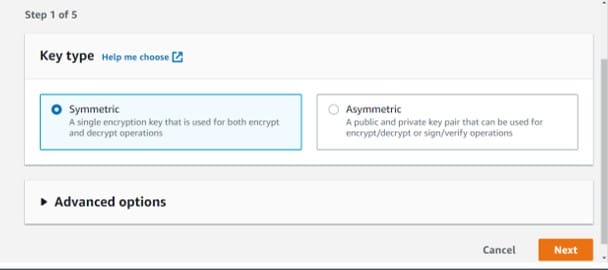
Create CMKs in Custom Key Store – select symmetric option
It’s not possible to create asymmetric customer master keys in a custom key store.
Step 6.
Click on Advanced options.
Step 7.
From the Key material origin field, select “Custom key store (CloudHSM)”.
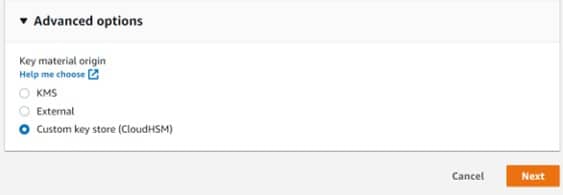
Create CMKs in Custom Key Store – CloudHSM
Step 8.
Click on Next.
Step 9.
Choose a custom key store for the newly created customer master key. (For making a new custom key store, you will need to click on Create custom key store)
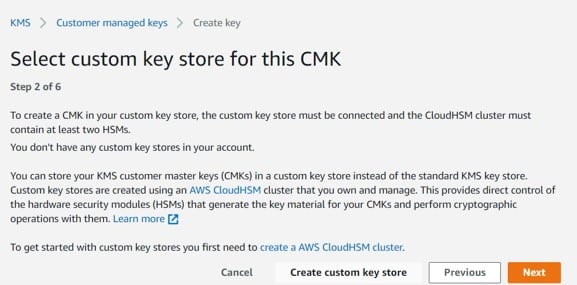
Create CMKs in Custom Key Store – create custom key store
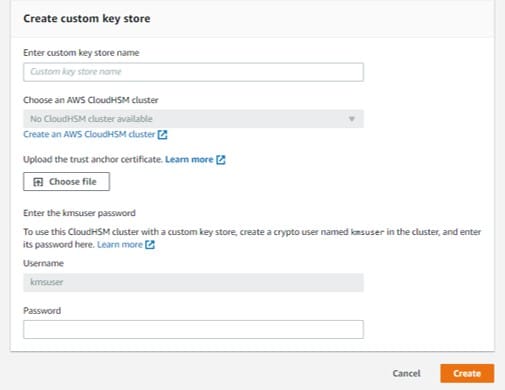
Create CMKs in Custom Key Store – custom key store
The custom key store which you choose will need to have a CONNECTED status. (active associated CloudHSM cluster, with a minimum of two active HSMs from differing Availability Zones)
Step 10.
Click on Next.
Step 11.
Fill in a specific alias + optional description for your customer master key.
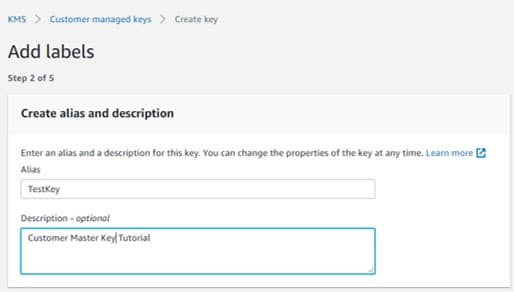
Create CMKs in Custom Key Store – add labels
Step 12.
Optional field: From the Add Tags page, start adding some tags to identify and categorize your customer master keys.
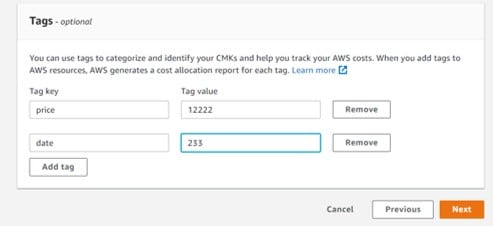
Create CMKs in Custom Key Store – add tags
Upon adding tags to resources, AWS starts generating a cost allocation report (In report there are tags for: usage + total costs)
Step 13.
Click on Next.
14. For Key Administrators field, choose which IAM users and roles that are allowed to manage the customer master key.
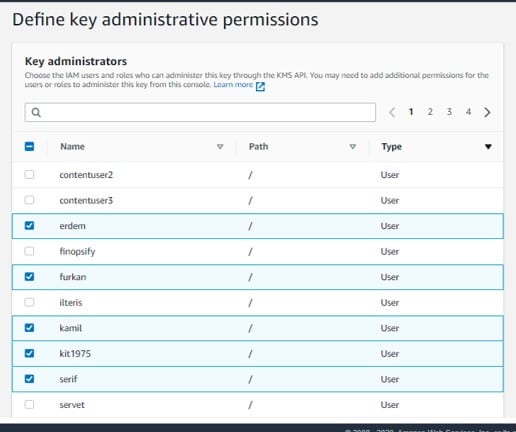
Create CMKs in Custom Key Store – key administrative permissions
Important to know:
IAM policies have the ability to promote other IAM users and roles with permission to utilize customer master keys.
15. Optional field: For the sake of preventing key administrators from deleting this customer master key, leave the box which is located at the bottom empty for the following option: “Allow key administrators to delete this key”.
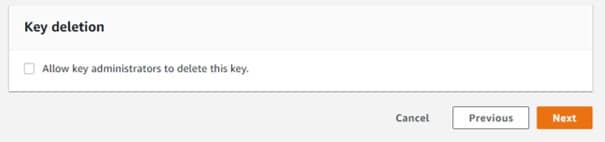
Create CMKs in Custom Key Store – key deletion
Step 16.
Click on Next.
Step 17.
For This account section, choose which IAM users and roles found in this AWS account who will get the ability to utilize the customer master key in cryptographic operations.
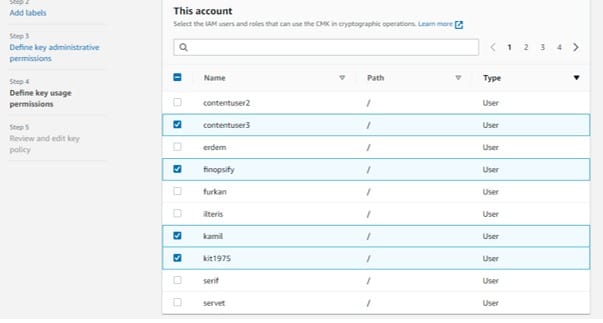
Create CMKs in Custom Key Store – this account
Important to know:
IAM policies may supply different IAM users and roles with the permission for utilizing the customer master key.
Step 18.
Optional field: It is possible for you to give permission to other AWS accounts for using this customer master key for cryptographic operations. If you wish to perform this move, head to the Other AWS accounts section at the bottom, select Add another AWS account and then fill in the specific account identification number of a specified external account. For adding more than one external account, you will need to repeat this same step.
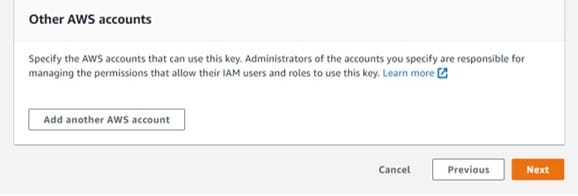
Create CMKs in Custom Key Store – other aws accounts
Important to know:
Administrators of other accounts need to allow access to the customer master key through the creation of IAM policies for their users.
Step 19.
Click on Next.
Step 20.
From Review and edit key policy page, you get the chance to reread and edit the policy document for your new customer master key. Upon completing the revision, select Finish.
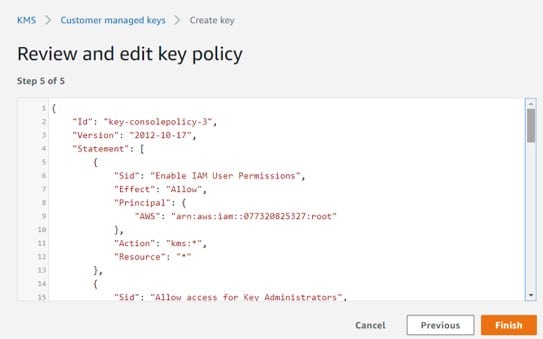
Create CMKs in Custom Key Store – review and edit key policy
- Upon reaching the finish of the process and it ends in a successful attempt, you will see the new customer master key in the custom key store which you had previously selected.
- Upon selecting a name or alias for the new customer master key, in its detail page you will find the following:
- The origin of the customer master key (CloudHSM)
- The name and the ID of the custom key store
- The ID of the CloudHSM cluster
– In case of failure in the process, you will get an error message which describes the reason for the failure
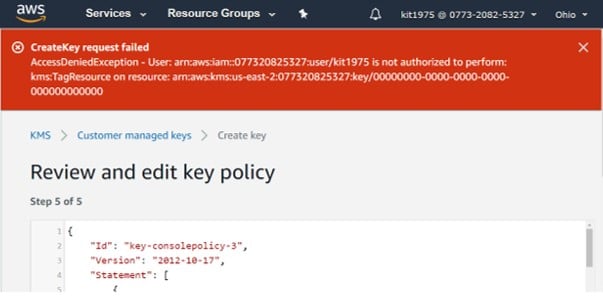
Create CMKs in Custom Key Store – CreateKey request failed
Hint:
For easily identifying customer master keys in a custom key store, do the following: From the Customer managed keys page, select and add Custom key store ID column. Select gear icon found in the top right and choose Custom key store ID.
read: S3 Inventory Consistency