This article provides a general overview about AWS Lambda, also highlights few of key features of AWS Lambda.
What is an AWS Lambda and What is it Used For?
- Lambda is one of the responsive cloud service and completely manages its infra.
- It checks activity within the application and responds by distributing codes, as in functions, defined by the user.
- For Lambda, AWS spreads the compute resources across multiple availability zones and it automatically scales them upon triggering of new actions. There is no need of user intervention.
- Lambda supports diverse programming languages like Node.js, Python and Java etc. The service can also run processes in languages that work with Amazon Linux such as Bash, Go & Ruby.
Things to know while using AWS Lambda:
- The Lambda function code should be written in a stateless style.
- No function variable should be declared outside of the reach of the handler.
- Sets of +rx permissions should be found on files of uploaded ZIP in order to make sure that Lambda will be able to execute this code for you.
- Old Lambda functions should be surely erased when they are not needed any more.
AWS Lambda Features:
Offer different resources some custom logic
Users can add custom logic to use Lambda with other services (S3 Buckets, SNS, EC2…).
Customizable back-end services
Get some newly created back-end services for selected apps which will be triggered on-demand through Lambda or custom API endpoints for API Gateway.
Add the code of your choice
Using AWS Lambda, user don’t need to use any new tools, frameworks etc. Lambda support embedding which-ever third party libraries using Lambda Layers.
Total automation for administration
AWS Lambda takes care of backend infrastructure for running code with high availability and fault-tolerance so that users get the chance to concentrate on developing unique back-end services.
Fault tolerant
Fault tolerance comes as default for AWS Lambda. AWS takes care about that in the background
Automated scaling
AWS Lambda will only invoke your code whenever required & AWS takes care of scaling for supporting incoming requests.
Connection with relational databases
RDS Proxy may be utilized for benefiting from completely managed connection pools for your selected relational databases.
Handle performance
With provisioned concurrency users can attain better manageability over serverless app’s performance.
Capability of connecting with shared file systems
AWS Lambda’s Elastic File System allows users to securely write, persist & read great volumes of data while maintaining low latency.
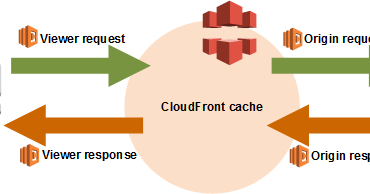
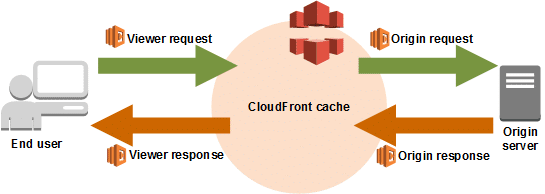
Running code with CloudFront requests
With Lambda@Edge, AWS Lambda is capable of running code over global Regions as a response to CloudFront events.
Having multiple functions
Multiple Lambda functions can be run for some hard and constantly-running tasks through workflows with Step Functions.
Top security model
AWS Lambda allows coding to get access to different services using it’s SDK and integrates with IAM while securely to execute code in a VPC.
Pay as you go
with AWS Lambda you will only need to pay as you go for the amount of execution you use.
A resource model with flexibility
You are capable of selecting how much memory you want to work with.
How is AWS Lambda Configured?
First: Go and sign into your AWS account.
Second: Head to AWS Services section and choose Lambda under “Compute”.
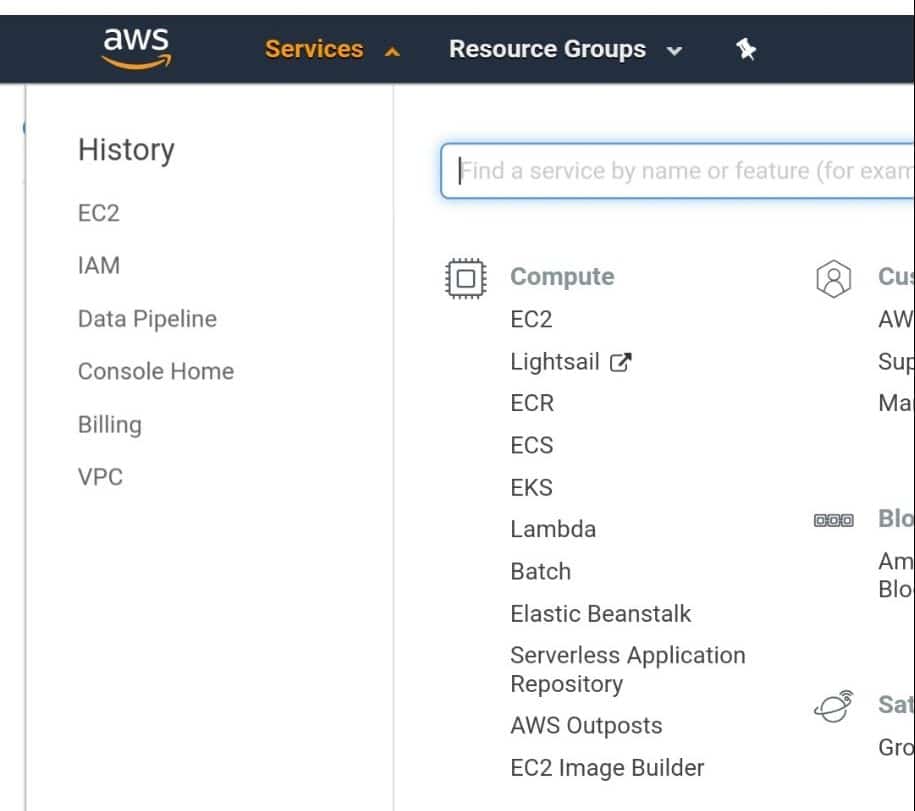
AWS Lambda – AWS Lambda from Compute Services
Third: Click on Create Function on top right. A new form will open.
Fourth: Before proceeding click on the Blueprint box in the center. Type the word “Hello” in the search box, and press Enter. Select the Blueprint with the name “hello-world-python” and click Configure.
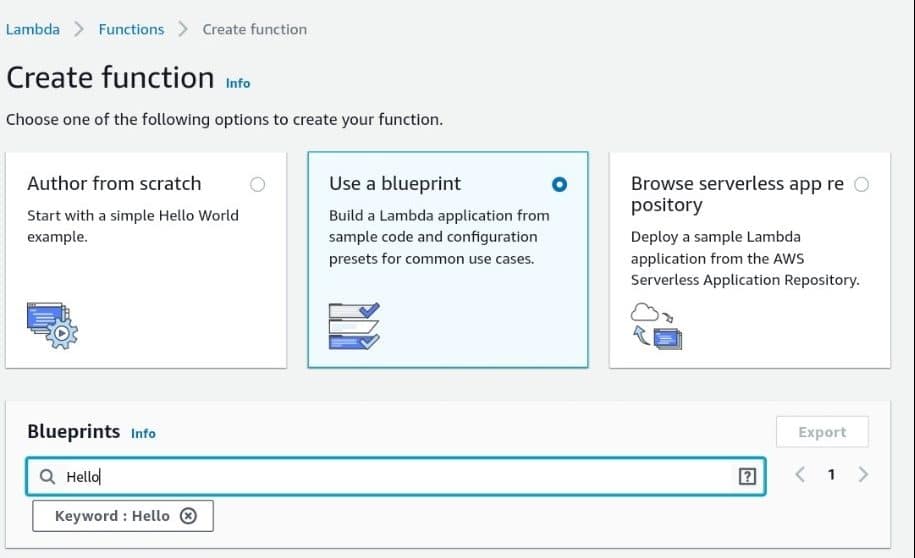
AWS Lambda – AWS Lambda Use a Blueprint
Fifth: Fill in the required information in order to create a Lambda function. Choose a unique name for your function, put the Execution role as “existing role”, and select the basic execution role for the Existing role box.
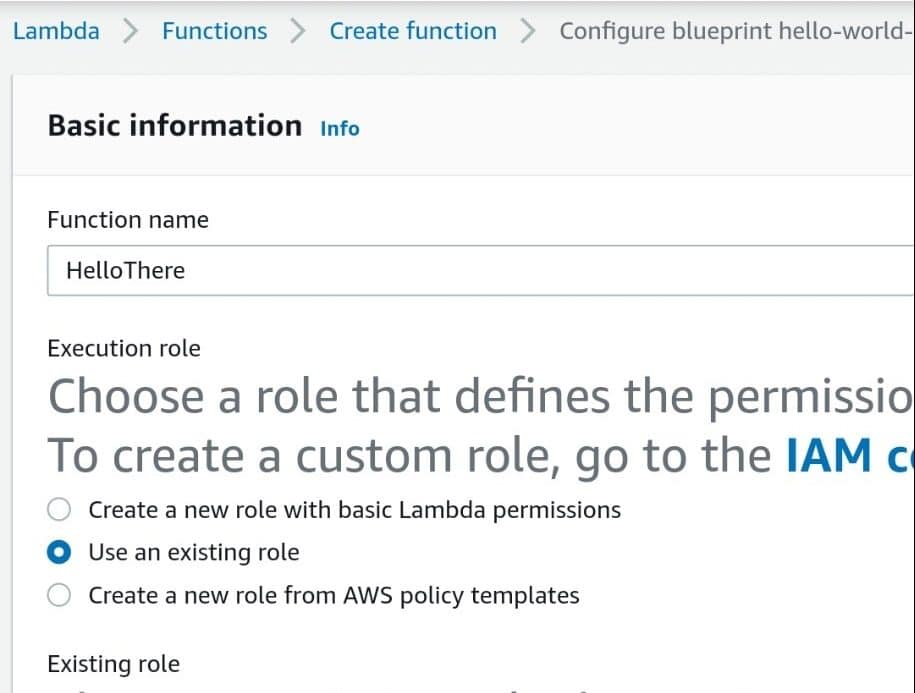
AWS Lambda – AWS Lambda Use an existing role
Sixth: Click on the Create Function button, and you’ve got yourself a new function.
AWS Lambda Limits
Limited Throttle
The maximum amount of throttle allowed is execution of 100 concurrent Lambda Functions for each AWS account. It includes the total concurrent executions of all functions found within the same region.
Formula for calculating number of concurrent executions per function:
(Average Duration of the Function Execution) X (Number of Requests or Events Processed by AWS Lambda).
Upon reaching throttle limit, an error will be returned having the code 429. When the duration of fifteen to thirty minutes passes, work can be resumed. You can increase throttle limit by contacting AWS support center.
Limited Resources
The below figure explains for you the resources limits for a Lambda function:
| Resource | Default Limit |
| Ephemeral disk capacity (“/tmp” space) | 512 MB |
| Number of file descriptors | 1,024 |
| Total number of processes and threads | 1,024 |
| Maximum execution duration per request | 300 seconds |
| Invoke request body payload size | 6 MB |
| Invoke response body payload size | 6 MB |
Limited Service
The figure below helps you know about the services limits for deploying a Lambda function:
| Item | Default Limit |
| Lambda function deployment package size (.zip/.jar file) | 50 MB |
| Size of code/dependencies that you can zip into a deployment package (uncompressed zip/jar size) | 250 MB |
| Total size of all the deployment packages that can be uploaded per region | 1.5 GB |
| Number of unique event sources of the Scheduled Event source type per account | 50 |
| Number of unique Lambda functions you can connect to each Scheduled Event | 5 |
Here are few awesome resources on AWS Lambda:
- CloudySave is an all-round one stop-shop for your organization & teams to reduce your AWS Cloud Costs by more than 55%.
- Cloudysave’s goal is to provide clear visibility about the spending and usage patterns to your Engineers and Ops teams.
- Have a quick look at CloudySave’s Cost Caluculator to estimate real-time AWS costs.
- Sign up Now and uncover instant savings opportunities.