EC2 Instances: AWS Status Check Alarms
How to Create and Edit Status Check Alarms?
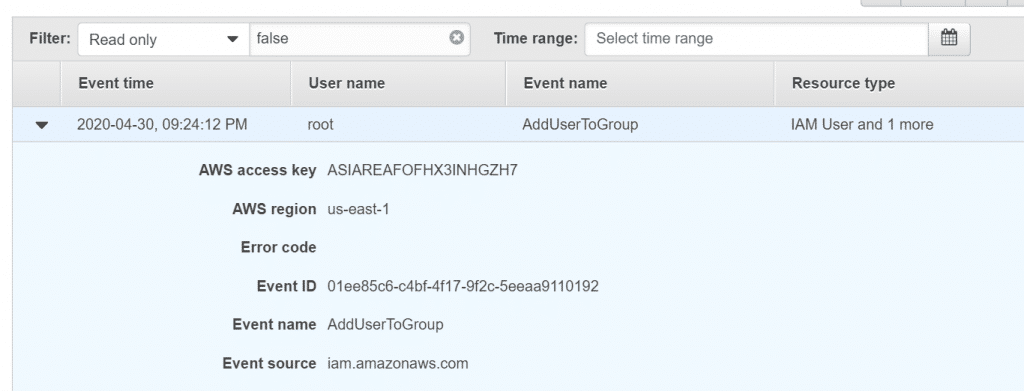
It is possible to utilize the status check metrics for creating status check alarms in CloudWatch alarms in order to notify you when an instance gets a failed status check.
Create a Status Check Alarm through the Console
Follow the below process for the sake of configuring an alarm that will send you a notification through your email, or stop, terminate, or even recover an instance whenever it fails in a status check.
How to create a status check alarm using the console?
- Go to the Amazon EC2 console through this link https://console.aws.amazon.com/ec2/.
EC2 Instances Status Check Alarms – EC2 Console
- From navigation pane, select Instances.
AWS Status Check Alarms – Select an EC2 Instance
- Choose an instance, select the Status Checks tab, then click Create Status Check Alarm.
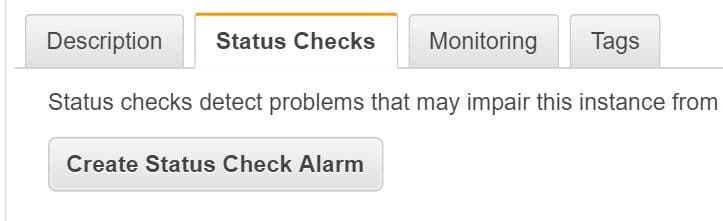
EC2 Instances Status Check Alarms – Click on Create Status Check Alarm
- Choose to Send a notification to. Select an already existing SNS topic, or otherwise click create a topic to create a new one. If you choose to create a new topic, inside With these recipients, type in your email address + addresses of other needed recipients while being separated by commas.
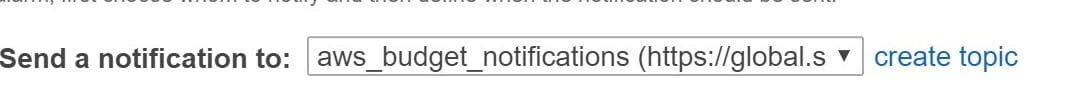
EC2 Instances Status Check Alarms – Add Recipients
- It is optional to click on Take the action, then choose the action you’d want to take.
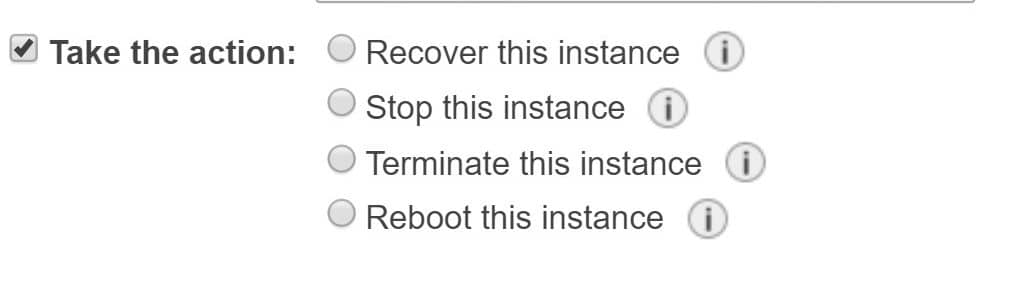
EC2 Instances Status Check Alarms – Choose an Action
- For Whenever, choose the status check you want to get notified about.
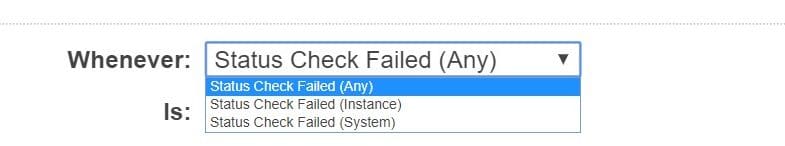
EC2 Instances Status Check Alarms – Choose Status Check to get Notified
If you have previously chosen Recover this instance during the prior step, choose Status Check Failed (System).
- In the section named For at least, specify what number of periods you’d like to evaluate and in consecutive section periods, choose the evaluation period duration prior to the triggering of the alarm and the sending of an email.

EC2 Instances Status Check Alarms – Enter Consecutive Periods
- As an optional step, In the section named Name of alarm, change the default name with a new name for the chosen alarm.
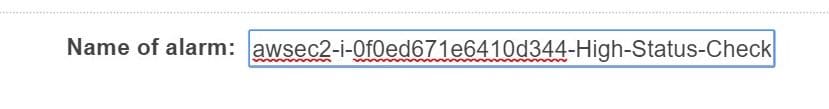
EC2 Instances Status Check Alarms – Enter a Name for the Alarm
- Click on Create Alarm.
EC2 Instances Status Check Alarms – Click on Create Alarm
Important Note
In case you have decided to add an email address to the list of recipients or otherwise went with creating a new topic, Amazon SNS will send you a subscription confirmation email message to every new specified address. Every one of the recipients needs to confirm the subscription by selecting the link included in that message. Alert notifications are going to be merely sent to the confirmed addresses.
In case you find yourself in need of making changes to an instance status alarm, you may simply choose to edit it.
Edit an AWS Status Check Alarm Using the Console
How to edit a status check alarm through the console?
- Go straight to the Amazon EC2 console using this link https://console.aws.amazon.com/ec2/.
- From under the navigation pane, select Instances.
- Choose one of the instances and select Actions, CloudWatch Monitoring, and Add/Edit Alarms.
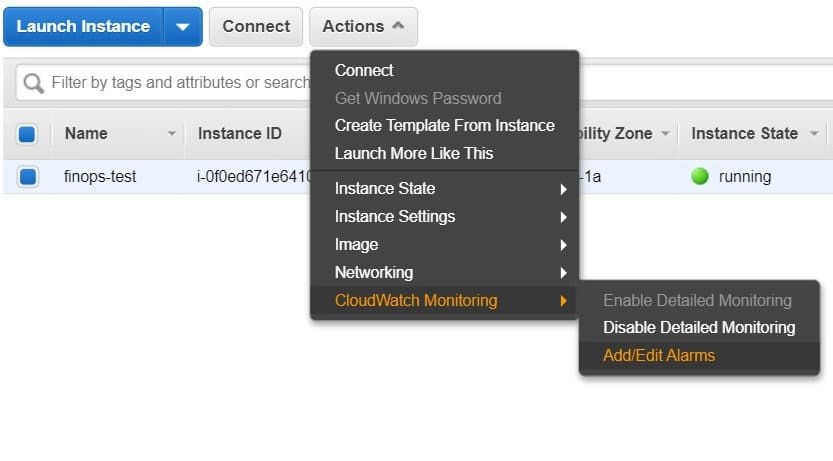
EC2 Instances Status Check Alarms – Add,Edit Alarms
- From inside the Alarm Details dialog box, select a name of an alarm.
- From inside the Edit Alarm dialog box, perform the required changes you want, then click on Save.
Create an AWS Status Check Alarm Through AWS CLI
In the below-mentioned example, you will see that the alarm is going to publish a notification to an SNS topic, arn:aws:sns:us-west-2:111122223333:my-sns-topic, as soon as the instance fails one of the following cases: the instance check or the system status check for a minimum of 2 consecutive periods. The CloudWatch metric which gets utilized here is the StatusCheckFailed.
How to create a status check alarm through the AWS CLI?
- Choose an already existing SNS topic or go ahead and start creating a new one.
- Utilize the below stated list-metrics command for the sake of viewing all of the available Amazon CloudWatch metrics for your Amazon EC2.
AWS Sloudwatch list-metrics –namespace AWS/EC2
- Utilize the below stated put-metric-alarm command for the goal of creating the alarm.
aws cloudwatch put-metric-alarm –alarm-name StatusCheckFailed-Alarm-for-i-1234567890abcdef0 –metric-name StatusCheckFailed –namespace AWS/EC2 –statistic Maximum –dimensions Name=InstanceId,Value=i-1234567890abcdef0 –unit Count –period 300 –evaluation-periods 2 –threshold 1 –comparison-operator GreaterThanOrEqualToThreshold –alarm-actions arn:aws:sns:us-west-2:111122223333:my-sns-topic
The period refers to the time frame taken in seconds, during which the Amazon CloudWatch metrics will get collected. In this mentioned example, the period used is 300, which means 60 seconds taken and multiplied by five minutes.
The evaluation period refers to the number of utilized consecutive periods during which the value of the metric is required to always be compared to the threshold. In this example, the value used is 2. The alarm actions mean the actions to be performed as soon as this alarm is triggered. In this example, the alarm to send an email is going to be configured through the use of Amazon SNS.
See Also