What is Azure Active Directory?
Azure Active Directory (Azure AD) is a cloud-based Identity and Access Management (IAM) service that provides corporate employees with secure access to external resources, such as Microsoft Azure Portal, Microsoft 365, and innumerable SaaS apps. Azure AD is used by IT admins, app developers, Azure, Office 365, Microsoft 365, or Dynamics CRM online subscribers.
In addition, Azure AD also facilitates access to internal applications on the company’s intranet and any cloud applications developed by that company. According to Microsoft, Azure AD defends against 99.9% of cyber-attacks using powerful features, including conditional Access, Multi-Factor Authentication (MFA), Single Sign-On (SSO), and more. Gartner recognized Microsoft as a 5-time leader in its Magic Quadrant for Access Management.
What is the Difference Between Windows AD and Azure AD?
When Microsoft released Windows 2000, the concept of Active Directory Domain Services was popular. The technology enabled enterprises to deal with multiple on-premise systems and applications through a single identity per user.
On the contrary, Azure AD offers an advanced Identity as a Service (IDaaS) system for an organization’s on-premise and cloud applications. The following sections gain insight into the difference between Active Directory and Azure AD.
Users Provisioning
Active Directory (AD) enables companies to manually create internal users via in-house or automated provisioning systems, including Microsoft Identity Manager.
On the other hand, Azure AD involves Azure AD Connect to synchronize identities to the cloud. Therefore, it supports the automatic creation of users from the cloud HR system. Moreover, Azure AD solution provisions identities in the SCIM-enabled SaaS applications to automatically provide applications with the necessary detail to enable user access. The SCIM stands for System for Cross-Domain Identity Management (SCIM).
External Identities (Guest Users) Provisioning
Active Directory features a dedicated external AD forecast where businesses can create external users manually. Unfortunately, as a result, managing the guest users’ lifecycle puts a massive burden on the administration.
On the other hand, Azure AD features a particular class of identity to support guest users. Azure AD B2B manages the link to the external user identity to validate the external user identity.
Credential Management
Active Directory involves several types of credentials, including smartcard authentication, certificate authentication, and passwords. AD manages passwords using password policies that include password complexity, expiry, and length.
Contrarily, Azure AD offers a robust password protection system for both on-premise and cloud users. This technology provides smart lockout and blocks custom and common password substitutions and phrases. According to Microsoft, the following categories are globally banned passwords:
- Product names
- Brand names
- Company-specific internal terms
- Locations related to the company
- Abbreviations associated with the company
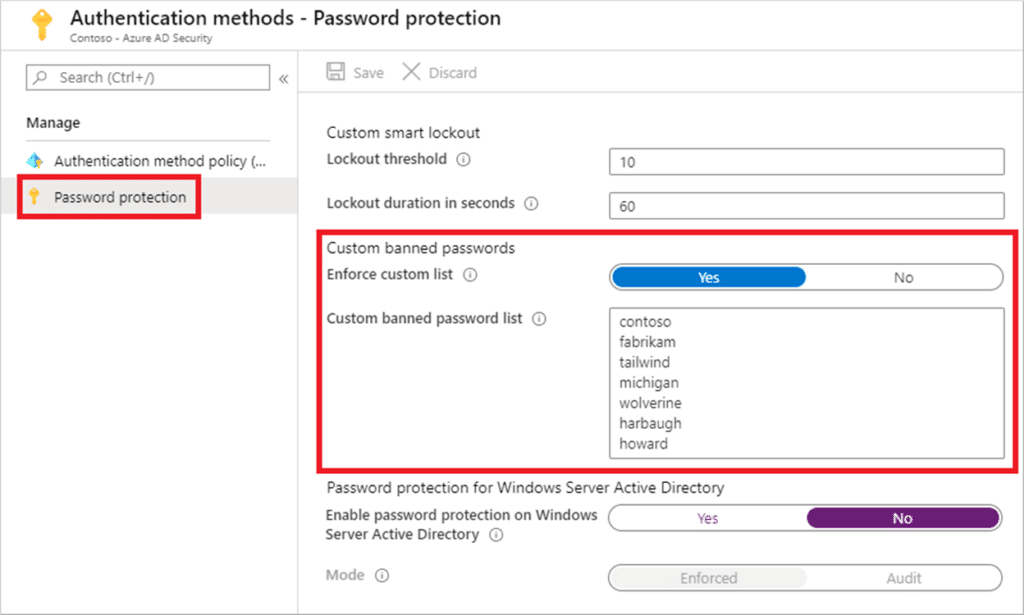
Figure 1: Custom Banned Passwords
In addition, Azure AD provides self-service password reset technology to reduce support costs. More importantly, passwordless technologies, such as FIDO2 and Multi-factor Authentication (MFA), add an extra security layer.
Administration Management
In AD, enterprises can employ a combination of domains, groups, and organizational units to assign admin rights to deal with Directory and other resources it may control.
Unlike AD, Azure AD delivers built-in roles with Azure AD’s Role-Based Access Control (RBAC). It can help assign roles with required permissions to manage Azure resources. In addition, Privileged Identity Management (PIM) can help enhance the management of roles. This system can offer time-restricted, just-in-time, or workflow-based access to privileged roles. As a result, organizations can manage, control, and monitor access to essential corporate resources.
Group Management
AD allows admins to add users in groups. For example, resource owners can grant group access to corporate resources and apps.
Like AD, group management is also available in Azure AD. Admins can manually assign membership or groups or utilize a query to dynamically incorporate users into the group. In addition, the Entitlement Management feature in Azure AD can help admins to grant users access to resources and apps using workflows and time-based criteria if necessary.
Infrastructure Applications
AD supports various infrastructure on-premise solutions, such as VPN, NPS, WiFi, IPSec, DHCP, and DNS. On the contrary, Azure AD doesn’t rely on networking controls. Instead, it offers a modern control plane to access applications and resources in this cloud world. In addition, Azure AD provides Conditional Access (CA), the latest security perimeter extended beyond an enterprise’s network to encompass devices and users’ identities.
Mid-Tier/Daemon Services
AD service accounts, or group Managed Service Accounts (gMSA), help services run in on-premise environments. After that, these applications inherit the service account’s permissions.
Contrarily, Azure AD uses managed identities to run applications in the cloud. Managed identities can be configured and used on Azure Virtual Machines (VMs).
Devices Support
The AD doesn’t directly support mobile devices. To this end, you may need 3rd-party apps. On the other hand, Azure AD integrates Microsoft Intune to support mobile and Windows devices. Conditional access can also be used to check if the attached device is a part of the authentication process. The AD also supports windows desktops.
Moreover, the AD enables the management of on-premise Windows Servers with the help of Group Policy or other management systems. Likewise, Azure AD supports Windows Servers using Azure AD Domain Services. It can provide NTLM or Kerberos authentication to apps that join Azure VMs to the managed domain.
Furthermore, the AD cannot natively support Linux/Unix operating systems. On the other hand, Linux/Unix VMs can utilize managed identities in Azure AD to access resources.
Line of Business Apps
LOB apps require modern authentication. To this end, businesses use AD FS with AD. Likewise, organizations can configure LOB apps with Azure AD to provide modern authentication.
SaaS Applications
Instead of supporting SaaS apps natively, the AD requires a federation system, like AD FS. On the other hand, Azure AD can integrate SaaS applications that support SAML, OAuth2, and WS-* authentication.
Top 10 Azure AD Features
Azure AD provides interactive and powerful features. The following sections delve into more details.
1. Single-Sign-On (SSO)
Azure AD features an SSO that automatically signs in users when they connect their BYOD with their company’s network. As a result, they don’t need to type a password to log in to Azure AD repeatedly. It is an easy way to access cloud apps without additional on-premise components. SSO can be applied with other sign-in methods, including Pass-Through Authentication or Password Hash Synchronization. However, it cannot be combined with ADFS – Active Directory Federation Services.
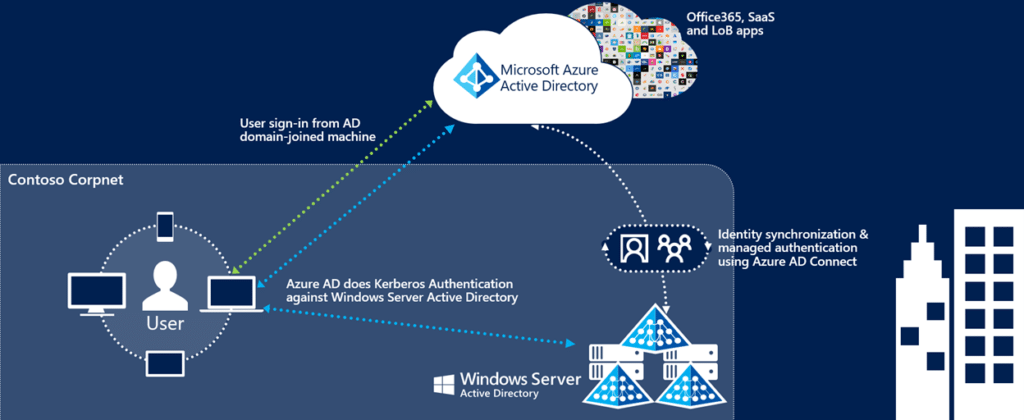
Figure 2: Azure AD SSO
2. Multi-Factor Authentication (MFA)
The MFA is a multi-step account login process that requires a user to present two or more pieces of evidence to get authentication successfully. The MFA increases cybersecurity because hackers cannot meet the second authentication requirement even if one factor or credential is compromised. Therefore, it will not be possible for them to access systems and networks. In addition, the MFA usually works on the following three factors:
- Something You Know (e.g., secret question or PIN)
- Something You Have (e.g., token or card)
- Something You Are (e.g., Biometric or Fingerprint)
Azure AD MFA also secures password reset. When a user registers for the Azure AD MFA, he can also register for the self-service password reset in one step. Azure AD MFA involves the following verification methods:
- Microsoft Authenticator
- Windows Hello for Business
- Authenticator Lite
- Voice Call
- SMS
- OATH Software Token
- OATH Hardware Token
- FIDO2 Security Key
3. Conditional Access (CA)
User and device identity have paramount importance in the modern cybersecurity ecosystem. The organizations can employ identity-driven signals, and CA can bring these signals together to help them make access control decisions and enforce their policies.
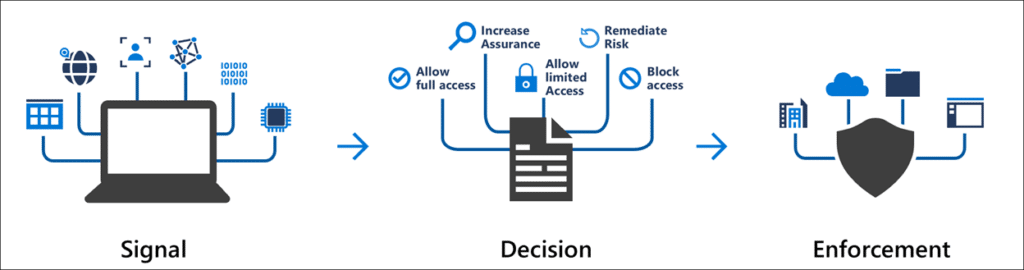
Figure 3: Conditional Access (CA)
As a matter of fact, the CA is based on conditions like “if-then statements,” also known as CA policies. So, for example, if a user wants to access a resource, he must fulfill the condition, such as meeting multi-factor authentication.
The following diagram demonstrates the application of CA policies requiring the meeting of MFA before granting access. If the user doesn’t fulfill MFA, the CA will deny access to apps and data.
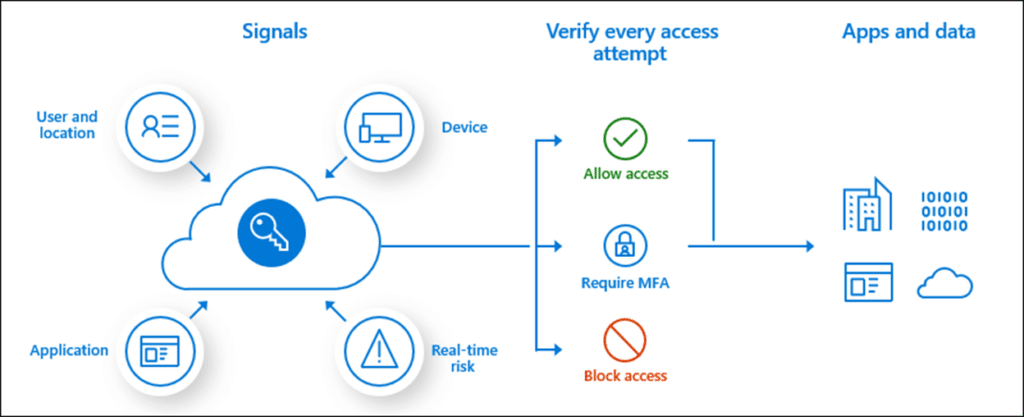
Figure 4: Conditional Access Policies
4. Identity Protection
Azure AD Identity Protection is a security feature that can help detect identity-based cybersecurity risks, such as malware-linked IP addresses, password spray, compromised credentials, etc. Moreover, Identity Protection can mitigate security threats and provide information on security events to help conduct investigations. This feature also involves several policies, including MFA Registration Policy, User Risk Remediation Policy, and Sign-in Risk Remediation Policy.
5. Application Management
Azure AD Application Management is a security solution to create, configure, manage, and monitor cloud applications. In addition, users can securely access the applications added to the Azure AD tenant.
This feature allows for grouping users and managing them as a collective. With Azure AD Group Management, administrators can easily and efficiently manage access to resources and applications. The feature can also help easily apply group policies for services, access controls, and governance provisions. Permissions to manage access resources are typically provided through roles in Azure AD.
6. Privileged Identity Management (PIM)
Azure AD PIM allows admins to manage, monitor, and control access to critical corporate resources. It also monitors the efficient and effective utilization of apps and resources. Such resources include Azure, Azure AD, Microsoft 365, and Microsoft Intune. As a result, organizations can reduce the attack surface by limiting access to such essential resources.
PIM also features just-in-time privileged access, as mentioned in the previous section. With this feature, admins can oversee what users are doing with their privileged access.
Another feature of PIM is that it alerts you when significant events occur in Azure AD, such as when a specific role is assigned or activated. PIM is available in Azure AD Premium P2 Licenses.
7. Azure AD Domain Name System (DNS)
Azure AD Domain Services include a DNS server that offers name resolution for a managed domain. The DNS server incorporates essential updates to run services and stores built-in DNS records. It allows for easier DNS management since the DNS records will employ the same credentials, APIs, tools, and billing as the other Azure services. In Azure AD, DNS maintains a database of services running on the network at any time.
Running your own services and applications requires you to create DNS records for systems not joined to the domain. In addition, you need to set up external DNS forwarders or configure virtual IP addresses for load balancers.
8. Azure AD Federation Services (ADFS)
ADFS provides simplified, secure identity federation Single Sign-On (SSO) capabilities in the cloud environment. Federation with Azure AD allows users to authenticate into the system using on-premises credentials and access all the resources. The deployment of ADFS can result in the organization achieving high availability and efficiency in its operations. The security of the authentication process is also enhanced with the use of Azure ADFS.
9. Reporting and Auditing
Azure AD also includes auditing and reporting features to track user and administrative activities in the cloud, such as changes in the configuration setting. Doing so can also help in complying with data protection requirements. Azure AD also provides search and investigation services to drill down on issues of interest. In addition, you can get quick access to reports, especially for SharePoint and Exchange.
More importantly, Azure AD reporting provides a comprehensive view of your cloud environments. The data on reports allow you to:
- Determine how your users are using services and applications
- Detect security risks to your organization
- Troubleshoot potential issues impacting business continuity
What Do I Need to Know About Azure AD Integrations?
The following sections take a deep dive into understanding Azure AD integrations.
Microsoft 365 Integration
Microsoft 365 involves Azure AD to deal with user identities surreptitiously. Free Azure AD subscription is available in Microsoft 365 paid subscription. This can help you integrate your on-premise AD DS to set up a single sign-on, synchronize passwords and user accounts, or SaaS apps like Dropbox and Salesforce.
Azure Service Integration
Service integration enables easy access to the Azure portal and various SaaS applications. Azure AD offers two services to be integrated: Logic Apps and Azure API Management. The former enables organizations to create and automate workflows, while the latter allows software developers to maintain, monitor, and secure APIs in the development environment.
Another key feature of Azure service integration is the Azure Service Bus, a solution to connect on-premises and cloud-based applications typically used for messaging workflows.
Best practices for migrating on-premise AD (Windows AD) to Azure AD
Since on-premise servers cannot be moved to the cloud, they are gradually disappearing. Cloud has been revolutionizing the digital world for a couple of years. That is the reason organizations are migrating on-premise AD to cloud-based Azure AD. Look at the following sections for help.
Undertake Effective Planning
Planning the migration strategy, that is, how you carry out the migration, is critical. As part of planning, decide which users will be migrated and the security settings for the cloud environment before the start of the migration process from Windows AD to Azure AD.
Perform device configuration and ensure the correct configuration settings are in place. It is the most time-consuming aspect of the migration process.
Provision Accounts
All users should have valid accounts for both the on-premises environment and the Azure AD environment before the start of the migration process.
Perform Assets Inventory
- Inventory the existing infrastructure before starting the migration process. Doing so can assist in understanding the environment.
- Register devices to AutoPilot using a Hardware Hash solution and reset the machines.
- Remove client workstations from the domain
Implement Azure Connect
Decommission on-premises server Identities from AD will then be synced to Azure AD using the Azure Connect synchronization tool. Additionally, Azure AD Connect provides seamless SSO functionality.
If there are any group policies, they should be exported from the server and migrated to Microsoft Intune, while existing files should migrate to SharePoint.
Ensure Resilient Back up
Create a resilient backup process of the onsite AD environment before commencing the migration process. Effective backup is critical in roll-back if necessary.
Strong Access Controls
Ensure the use of the same user accounts in both environments. You can implement Hybrid Identity to achieve strong user accounts in both environments. Ensure that identities are effectively managed across both environments. Finally, implement Azure AD Tenant to simplify the management of user accounts and group policies.
Apply Correct Applications Configuration
All applications should be compatible with Azure AD before undertaking the migration process. Additionally, ensure that all applications are integrated into Azure AD authentication functionalities. If some applications hold data repositories, it should be possible to connect back to these as long there is an effective authentication process.
Perform Pilot Migration
When you successfully implement the previous practices, you can migrate the data. To this end, look at the following points.
- Start with the less critical data and applications first to reduce risk in case of an ineffective rollover.
- Implement automated tools to manage the migration. Examples of such tools include Azure Automation. Azure Automation runs Runbooks to manage migration and subsequent configuration requirements.
- Apply the bulk update solution to identify target on-premise devices for migration to Azure AD.
- Once a device appears in Azure AD, its record must be cleared from on-premises records.
- Activate a sync in Intune and permit it to push applications through the migration process to speed it up.
Reconfigure Windows Services
Restore the windows test after the Pilot Migration process. After migration, reconfigure those applications that rely on Windows AD to work with Azure AD. Doing so often involves the creation of additional user accounts compatible with authentication mechanisms in Azure AD, such as OAuth or SAML.
Test
Test the entire migration process before going live. To this end, you must ensure all users can authenticate successfully with their newly assigned credentials. Furthermore, ensure all applications work correctly in the new Azure AD environment.
Perform Full Migration
Follow the steps below to perform full migration.
- If you satisfy, perform a complete migration.
- Monitor the new solution closely after going live.
- Identify areas for improvement and troubleshoot issues and optimize performance.
- Security settings should also be constantly reviewed to enforce access control policies in the new environment continuously.
Sources
https://learn.microsoft.com/en-us/azure/active-directory/authentication/concept-password-ban-bad
https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/overview
https://www.varonis.com/blog/azure-active-directory
https://learn.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-sso
https://www.cisa.gov/resources-tools/resources/multifactor-authentication-mfa
https://learn.microsoft.com/en-us/azure/active-directory/authentication/concept-mfa-howitworks
https://learn.microsoft.com/en-us/azure/active-directory/develop/v2-app-types
https://learn.microsoft.com/en-us/azure/active-directory-domain-services/manage-dns
https://learn.microsoft.com/en-us/azure/active-directory/reports-monitoring/overview-reports
https://learn.microsoft.com/en-us/microsoft-365/enterprise/azure-integration?view=o365-worldwide
See Also